In an age where cyberattacks and data breaches dominate headlines, safeguarding digital identities has never been more urgent. Enter One-Time Passwords (OTPs)—a cornerstone of modern cybersecurity. Whether you’re logging into your email, confirming a bank transfer, or securing a corporate network, OTPs provide a critical layer of defense. But what exactly does OTP mean, how does it work, and why is it indispensable? This Complete guide demystifies OTPs, exploring their mechanics, applications, vulnerabilities, and future.
Understanding OTP: Definition and Core Principles
OTP stands for One-Time Password, a unique, short-lived code used to authenticate users during a single transaction or login session. Unlike static passwords, which remain valid indefinitely, OTPs expire within seconds or after one use, making them virtually useless to cybercriminals even if intercepted.
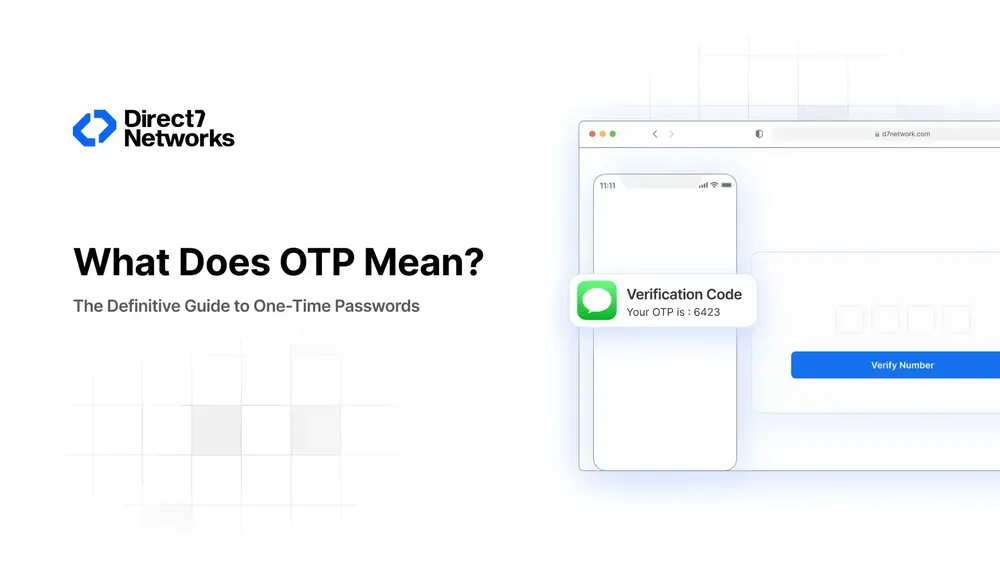
OTP Meaning in Text Messages
When people search “what does OTP mean in a text message,” they’re often referring to SMS-based OTPs. These codes are sent via text to a user’s mobile device, acting as a second verification step. For example:
“Your D7 Networks OTP is 8H4K9L. Expires in 3 minutes.”
This method is widely adopted due to its simplicity and accessibility, though newer technologies like authenticator apps are gaining traction.
The Evolution of OTPs
OTPs originated in the 1990s with hardware tokens like RSA SecurID, which generated codes using built-in algorithms. As mobile phones proliferated, SMS OTPs became the go-to solution for businesses and consumers. Today, OTPs are a pillar of multi-factor authentication (MFA), combining:
- Something you know (password).
- Something you have (phone or token).
- Something you are (biometrics, in advanced systems).
Why Are OTP Messages Important?
OTP messages play a critical role in modern cybersecurity by adding an essential layer of protection beyond traditional passwords. They mitigate risks associated with password breaches, phishing, and credential theft. For businesses, OTPs help build customer trust, ensure compliance with data protection regulations (e.g., GDPR, PCI DSS), and reduce financial losses from fraud. For users, they provide peace of mind, knowing that even if their password is compromised, an attacker cannot access their account without the temporary code.
How OTPs Work: A Deep Dive into Algorithms and Protocols
OTPs rely on cryptographic algorithms to ensure randomness and security. Here’s how they operate behind the scenes:
1. OTP Generation Methods
- Time-Based OTP (TOTP):
Uses a shared secret key and the current timestamp (e.g., 30-second intervals) to generate codes. Apps like Google Authenticator and Authy use TOTP.
Example: Code = HMAC-SHA1(Secret Key, Current Time) - HMAC-Based OTP (HOTP):
Relies on a counter incremented after each use. Common in hardware tokens.
Example: Code = HMAC-SHA1(Secret Key, Counter) - SMS/Email OTP:
Randomly generated by a server and sent via text or email.
TOTP vs HOTP: Key Differences
| Feature | TOTP (Time-Based) | HOTP (HMAC-Based) |
|---|---|---|
| Trigger | Time-synchronized | Counter-based (event-driven) |
| Expiration | 30–60 seconds | After single use |
| Use Cases | Authenticator apps (e.g., Google Authenticator) | Hardware tokens (e.g., YubiKey) |
| Security Risks | Relies on device clock sync | Vulnerable to counter desync if codes are generated but unused |
2. OTP Delivery Mechanisms
- SMS: Instant delivery to mobile devices but vulnerable to SIM-swapping.
- Email: Accessible across devices but risky if the email account is compromised.
- Authenticator Apps: Generate codes offline, immune to network delays.
- Voice Calls: Useful in areas with poor SMS connectivity.
3. Validation Process
The authentication server regenerates the OTP using the same algorithm and compares it to the user’s input. If they match and the code hasn’t expired, access is granted.
Why OTPs Are Secure
- Short Lifespan: Codes expire quickly, reducing the window for misuse.
- Unpredictability: Algorithms ensure codes can’t be guessed.
- Multi-Factor Layer: OTPs add a second verification step, thwarting password-only breaches.
Types of OTPs: Pros, Cons, and Use Cases

Different OTP methods cater to varying security needs and user preferences:
1. SMS-Based OTPs
Pros:
- No app installation required.
- Ideal for users with basic mobile phones.
- High adoption rates (e.g., 80% of 2FA systems use SMS).
Cons:
- Vulnerable to SIM-swapping and SS7 attacks.
- Network delays can cause expiration issues.
2. Authenticator Apps (TOTP)
Pros:
- Offline functionality.
- Resistant to phishing and interception.
Cons:
- Requires smartphone ownership.
- Setup can be complex for non-tech users.
3. Hardware Tokens (HOTP)
Pros:
- Immune to malware and phishing.
- Used in high-security environments (e.g., government agencies).
Cons:
- Costly to distribute and replace.
- Risk of loss or theft.
4. Email OTPs
Pros:
- Works on any internet-connected device.
- Useful for account recovery.
Cons:
- Email breaches can compromise OTPs.
- Slower delivery compared to SMS.
Why OTPs Are Essential for Modern Security
Mitigate Password Vulnerabilities:
- Over 80% of breaches involve stolen or weak passwords. OTPs neutralize this risk by adding a dynamic layer.
Compliance with Regulations:
- GDPR, PCI DSS, and HIPAA mandate MFA for protecting sensitive data.
User Convenience:
- No need to remember complex passwords; codes auto-expire.
OTP Use Cases Across Industries
Banking & Finance:
- Authorizing wire transfers, logins, and card-not-present transactions.
- Example: A user receives an SMS OTP to confirm a $10,000 transfer.
Healthcare:
- Securing patient portals and EHR (Electronic Health Record) access.
E-Commerce:
Verifying high-value purchases and account changes.
Enterprise Security:
- Protecting VPNs, cloud platforms, and internal systems.
OTP Security Risks and Mitigation Strategies
No system is bulletproof. Key challenges include:
1. Phishing Attacks
- Risk: Fraudsters trick users into sharing OTPs via fake login pages.
- Solution: Educate users to never share codes and deploy anti-phishing tools.
2. SIM-Swapping
- Risk: Hackers port a victim’s number to a new SIM card to intercept SMS OTPs.
- Solution: Use app-based OTPs or biometric verification as backups.
3. Man-in-the-Middle (MitM) Attacks
- Risk: Attackers intercept OTPs during transmission.
- Solution: Encrypt OTP delivery channels and use time-bound codes.
Best Practices for Implementing OTPs
For Businesses:
- Choose Reliable OTP Providers: Prioritize platforms like D7 Networks with high deliverability rates and global reach.
- Enable Rate Limiting: Block brute-force attacks by limiting OTP attempts.
- Offer Multiple Channels: Let users choose SMS, email, or app-based OTPs.
For Users:
- Avoid Public Wi-Fi for OTPs: Use secure networks to prevent interception.
- Monitor Accounts: Report unauthorized OTP requests immediately.
The Future of OTPs: Innovations and Trends
Biometric Integration:
Pairing OTPs with fingerprint or facial recognition for hybrid security.
AI-Powered Fraud Detection:
Machine learning algorithms flag suspicious OTP requests in real time.
Passwordless Authentication:
FIDO2 and WebAuthn standards aim to replace passwords with OTPs and biometrics.
Conclusion: Embracing OTPs for a Secure Digital Future
OTPs have revolutionized cybersecurity, offering a simple yet robust way to protect identities and transactions. While challenges like phishing persist, advancements in encryption, AI, and biometrics are enhancing their resilience. For businesses, integrating OTPs through trusted providers like D7 Networks ensures compliance, boosts customer trust, and thwarts cyber threats.
As technology evolves, so will OTPs—adapting to stay ahead of hackers and pave the way for a passwordless world. By understanding their mechanics and adopting best practices, users and organizations alike can harness the full potential of OTPs to secure the digital landscape.